The Cloud is about to Crush the Hardware-based Security Industry

Last week Amazon announced another stellar quarter, with AWS again being the main headliner for the ecommerce high flyer. Yet I’m convinced AWS growth and profitability has even deeper implications for traditional hardware-bound network security vendors. Two weeks ago, I spoke with a CISO at forward-thinking IT shop. It was one of the most encouraging and thought-provoking IT discussions I’ve had in a while. He said they were betting on the cloud to “transform” their security posture by enhancing security and scale and reducing costs and complexity.
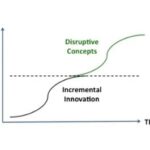
The Cloud as a Driver of Security Transformation
This is a substantial shift in thinking from just a few years ago when the cloud was seen as being less secure by most CISOs. While I’ve certainly seen the enterprise cloud shift firsthand, most of the drivers were operations-driven. IT wanted more agility and scale or some cost savings for unpredictable or seasonal workloads. Security concerns were seen by many as obstacles to cloud migration. That has clearly changed.
Why? Here is a list of factors that will drive the cloud software security transformation.
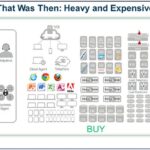
1. Consolidation of Buyers; Commoditization of Hardware
Digitalization will add to cloud delivery pressures and force IT into more software and services and away from hardware-defined tradeoffs. This, combined with buyer consolidation and commoditization, will make IaaS and managed service providers (and best practice enterprise shops) powered by software-defined capabilities much more influential than the traditional hardware vendors.
3. Software and Services are Strategic to Security and Scale
After decades of innovation aimed at hardware differentiation and specialization as a means of growth and profitability the tables have turned and vendor operating models will need to shift to survive. The virtualization, software and cloud-defined benefits of scale and agility will embrace security in ways that simple weren’t possible in complex networks of devices architected for simpler, slower times, manageable security demands and single vendor networks.