Verizon’s 2017 Data Breach Investigations Report (DBIR) is a detailed study of cyber threats. Subsequently DBIR provides an ideal analytical framework for enterprises seeking to reduce cyber risk.
An easy way to get into Verizon’s DBIR is look at the biggest numbers to see where the cyber threats are. A quick glance of page 3 shows that 75% of attacks were by outsiders, 81% used stolen credentials, emails based malware was in 61% of attacks and criminal organizations were involved 51% of the time (they want to sell the data). While the aggregate numbers reconfirm our intuition it’s useful to carefully read the DBIR from an enterprise perspective.
Looking at the enterprise component within the 8 industry sectors in the DBIR we see that compute devices (whether company owned, personal or partner) is where all the action is. A common attack pattern was credential theft from malware leading to a data breach.
Enterprises could reduce cyber risk by ensuring no compute device ever got hacked but that seems both expensive as well as impossible. Maintaining a high level of trust for all devices connecting to enterprise apps has never worked for large organizations. A more practical approach is to align the level of trust with the value of the application – i.e. the higher the value of the app, the greater of level of trust we want to verify. Conceptually, we want a trust-based access control to reduce our cyber risk.
Utilizing Verizon’s DBIR incidents as a rough guide we can create 3 trust categories:
informational apps, mission critical apps and enterprise infrastructure. For Internet-facing apps we want to mandate multi-factor authentication as a counter-measure to credential theft (seen in 81% of attacks). For the next level up in value, mission critical apps, we’d want to require MFA plus posture checking to ensure malware isn’t running while the device is connected to the enterprise. And for those few devices that manage the enterprise infrastructure we’d want to require MFA plus posture checking plus integrate a machine-learning based endpoint protection system to ensure that malware has never been present (or is fully contained).
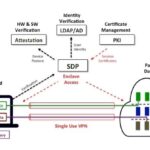
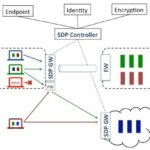
The key factor to making a trust-based access control system work is to ensure compromised devices cannot jump tiers. Thus malware on device accessing an informational site should not be able to re-task the application server and pivot to the data center. We can keep devices from jumping trust levels by provisioning access at an application layer.
Application layer access control works by provisioning connectivity from an app “inside” the user’s compute device to a port on the application server. For example in a device accessing an informational web site, only the browser on the authorized device would be able to connect to port 80 or 443 on the web server. Thus malware on the compromised compute device would be outside the application tunnel. And even if malware could hypothetically inject commands into the layer 4 tunnel, they would not be able reach the correct port of the application server.
To date, such trusted access control solutions were limited to financial institutions and government agencies. However Indecium has developed a new Trusted Access Control solution that integrates trust verification and application layer connection management into a single product. Trusted Access Control allows enterprises to reduce cyber risk by ensuring that attacks by outsiders (75%) using stolen credentials (81%) and malware (61%) to steal data so it can be sold by criminal organizations (51%) doesn’t happen!