A Flicker Of Light: A New Security Stack Points The Path To Safety
The last few years have been a difficult time for those who protect data. Defense-in-depth, the gold standard in cyber security, has failed. The basis behind defense-in-depth is to deploy redundant layers of security products to defeat every part the cyber kill chain. Unfortunately inside attacks and compromised devices belonging to authorized users operate within the protective bubble making them difficult to stop or even detect. Further complicating matters, the shift from company owned and operated to personal and public compute resources.
In panic, many organizations deployed more security products or utilized VDI to create virtual air gaps. Sadly the short-term fixes often created new vulnerabilities or impeded end-to-end visibility. But now security professionals are testing a new security stack that utilizes a small set of interlocked security controls to stop a wide range of attacks.
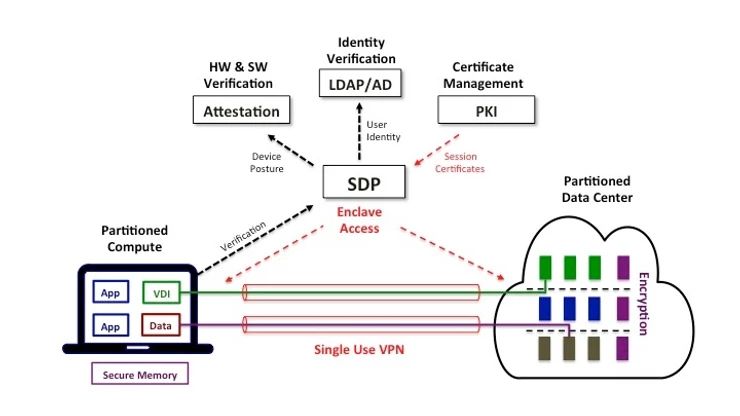
The new stack design is very simple – an isolated compute partition on the user’s device is connected to an isolated compute partition in a data center with a single use VPN connection. Before connectivity is provisioned, the hardware identity and software hashes from the user’s device are checked. End-to-end encryption is implemented via tamper resistant memory. Once inside the enclave, authorized users are able to access protected applications as well as encryption and VDI services. Conceptually the new security stack is a hardware-based virtual enclave.
The key design element of this security stack is that at least three controls must simultaneously unlock for enclave access. This is similar to a bank vault with multiple combination locks except for one important difference – the thieves must get everything right on the first attempt. For example, enclave access requires a valid hardware token, certificate exchange and device verification all to be approved in the same connection. If anything fails, an alarm is generated!


