Stop Catastrophic Cyber Failure: The Value of a Threat-based Security Strategy
In the last segment of the “Threat Based Security Model” series we’ll highlight the value of a threat-based model.
Imagine you are wheeled into a hospital emergency unit and immediately given a heart transplant. No one asks you questions about why you are there. The decision to operate is based on a survey of others your age. After the transplant, the hospital sends you home without even checking to see if you are fit to be released.
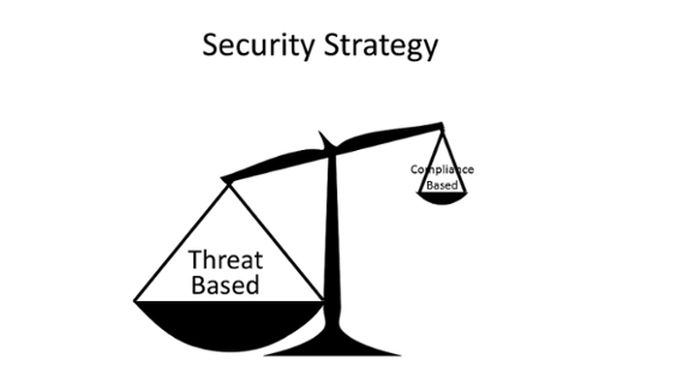
Fortunately, this Kafka-ese scenario is not how the medical industry operates. But, this is how compliance-based security works.
Compliance-based security doesn’t ask you what the relevant threats are to your organization. It goes right into “surgery” based on the risks seen at other companies. Compliance-based security also mandates complex solutions that often create more vulnerabilities than eliminating them.
ACT starts with a threat assessment to identify where the greatest risks for your organization lie. Based on your organization’s specific risk profile, you are in a better position to develop a comprehensive plan for protecting the data and the underlying compute infrastructure, which is defined by group. To execute this plan, implement the least invasive security controls— starting with access control, then data encryption and process isolation as appropriate for each group. Finally, implement penetration tests to ensure that the security controls have done their job. If the pen test fails, feed the results into the threat assessment model and repeat the process. The ACT model is designed to give you control, starting with the least invasive approach. This is where Software Defined Perimeter (SDP) comes in.
SDP is the least invasive security control because it leaves the compute devices and the data untouched. SDP integrates access control, policy enforcement and cryptographic verification, enabling the segmentation of users, devices and compute resources into groups. Once SDP defines groups, data encryption and process isolation can be added if necessary. Just as in the case of medical care, the least invasive procedure is implemented first (in this case access control) before adding more invasive procedures to improve the outcome.


